DocuSign user information found through Google search
As the world’s largest electronic signature platform, DocuSign says that they have over 6 million unique signers processing millions of transactions per year and that they are “trusted by more people, more companies, more times than any other electronic signature provider in the world.”
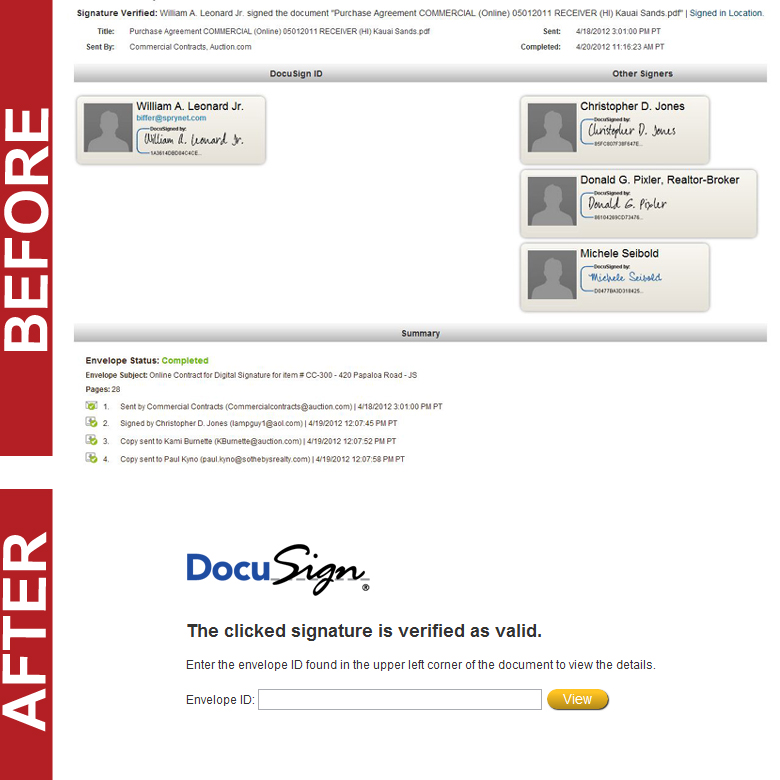
In just one search query in particular, we uncovered 4,450 URLs filled with DocuSign customer names, emails, document names, and GPS coordinates of where documents were signed. These details are found on websites with URL structures appearing like the one below (which is not a functional link that takes you to a signed document, just an example):
[ba-quote]https://www.docusign.net/Member/DocuSignTrust.aspx[/ba-quote]
DocuSign tells AGBeat that while the documents appear to be hosted on their secure https servers, “They are not. Anything that is found via Google search is not from DocuSign’s secure site, but rather the publicly accessible and searchable locations where customers have saved their personal copies of signed documents. In order to access documents, data, or transactions on the DocuSign Global Network, you must have the login credentials and password.”
We do not yet know the full scope of the number of transaction details that can be seen via Google, but we can see that they go as far back as at least January in our preliminary investigation. We have not made public how to discover these documents due to security risks, but suffice it to say that we can see the private emails, signatures, times, dates, locations, and document names (hypothetically speaking, we can see “Listing on 201 Main Street” or “Employment Contract – $58k/yr” as document names).
On the heels of a hacker leaking LinkedIn and eHarmony passwords, the leaking of personal information and potential details of legal documents that are meant to be private, is a major problem for several industries and feeds the hysteria behind cloud based storage and digital data sharing.
The company tells AG that “While DocuSign encourages customers to save their signed documents on the secure DocuSign Global Network, we are also required by law to offer customers the ability to download and retain their own personal copies,” adding that “it appears that a very small number of DocuSign users have saved their own personal copies of their signed documents to publicly accessible and searchable locations outside of the secure DocuSign Global Network. In the event that customers need to save signed documents in a location outside of DocuSign, we encourage that they ensure the location meets the security requirements of all signing parties.”
DocuSign asserts their “commitment to security” as outlined on their website. DocuSign is the official and exclusive provider of electronic signature for the National Association of Realtors’ nearly one million members, under the REALTOR Benefits Program, and is used by many industries, including users like American Airlines, LinkedIn, Sony, and Yamaha.
After publication, all links formerly discovered through a Google search appear to no longer be clickable, but can still be viewed through the Google cache, as seen in the before and after below.
The American Genius is news, insights, tools, and inspiration for business owners and professionals. AG condenses information on technology, business, social media, startups, economics and more, so you don’t have to.









































abodograph
June 7, 2012 at 2:07 pm
Nice work breaking the story!
jonbenya
June 7, 2012 at 2:15 pm
Wow, so glad I’m not on Docusign!
Market Leader
June 7, 2012 at 3:50 pm
Definitely something to be aware of. Thanks for sharing!
MatthewCohen
June 7, 2012 at 3:50 pm
I can see what you guys mean – but ask yourselves if the information disclosed is truly PII as defined in any state, or simply *might* be undesirable to have disclosed.
franklyrealty
June 7, 2012 at 5:29 pm
@MatthewCohen I had to google PII. I got this:
Personally Identifiable Information (PII), as used in information security, is information that can be used to uniquely identify, contact, or locate a single person or can be used with other sources to uniquely identify a single individual.
I would think that a private email address and private name with information that they signed an “offer to purchase 555 Oak” as being VERY personal information that can “uniquely identify” a person. And as for “locate a single person” it actually has the GPS coordinates of where the person signed. Is that PII enough?
MatthewCohen
June 7, 2012 at 5:41 pm
@franklyrealty – Again, I see what they mean – there is significance and some sensitivity, but read further into any state’s definition of PII and when it rises to the level of significance that must be disclosed it is almost always a first initial or first name and last name plus one or more of the following (1) Social security number. (2) Driver’s license number or State ID number. (3) Account number, credit or debit card number, in combination with any required security code, access code, or password that would permit access to an individual’s financial account. In some states the account number alone is sufficient, without the password.
franklyrealty
June 7, 2012 at 6:03 pm
@MatthewCohen Got it. No passwords here. Would showing the full contract be PII in your opinion? I wouldn’t be surprised if it was up there as well. I will look.
jonbenya
June 7, 2012 at 6:07 pm
@franklyrealty @MatthewCohen Showing the full contract would certainly be PII, IMHO. consider if the contract exposed was a cash offer with bank statement proof of funds, or copies of drivers licenses in the file. Also, a check copy with acct and routing numbers? That would make for a SERIOUS breach.
franklyrealty
June 7, 2012 at 6:14 pm
@jonbenya @MatthewCohen I just found one saying “Final Offer 555 OAK.pdf” (I changed the address). I would think this is very private information. I wouldn’t want other buyers knowing that I was offering on a house. Yes it could interfere with the deal.
jonbenya
June 7, 2012 at 6:21 pm
@franklyrealty What about the unique signature block and ID number below? Can that be used fraudulently?
MatthewCohen
June 7, 2012 at 6:35 pm
@jonbenya @franklyrealty The whole file would DEFINITELY be a serious breach!
franklyrealty
June 7, 2012 at 6:45 pm
@jonbenya Well the signature is usually not a real client wet signature in the sense that it wasn’t done with a pen (I think). And I don’t think that ID# can be used for anything useful to a hacker.
Missy Caulk
June 7, 2012 at 4:27 pm
Dang what is going on? I hate to hear this. Wonder why they have not notified us?
franklyrealty
June 7, 2012 at 5:27 pm
@Missy Caulk Because they don’t know. It has probably been on there for many months.
DanTroup
June 7, 2012 at 4:58 pm
While I think this is a good find, I don’t think it has the same weight as other breaches. If you could actually access the documents then I would say it was huge. Just names and email isn’t something I would stop using them for. If you found this on your own then I feel you should have brought it to DocuSign in private and allowed them to fix it. Once it was fixed, then publish your story.
Just because the pages were on https doesn’t mean they can’t be public. https is a protocal not a URL structure. https can be used for public or private websites where you want the data transfering between the user and web server to be secure. How that data is published on the server has nothing to do with https.
franklyrealty
June 7, 2012 at 5:21 pm
@DanTroup
Reagrding HTTPs, Yes, I think the point is, it is funny when companies use “httpS” in part to seem more secure. But it isn’t so secure if you just let Google index it.
So you would rather AG hold onto the information for a few days, while more customers expose themselves, vs telling Docusign first to try and fix it? Fix it how? It isn’t like Docusign can immediately remove the information from Google and Google Cache.
Sure they didn’t leak the full contract. Well, as far as we know. Maybe they did. But leaking unpublished private email addresses and any details of a private contract is horrible. We have to trust these companies. I just found a colleague of mine. I bet she will NOT be happy that THREE of her transaction details (not the contract itself) are on Google. Three over 6 months.
franklyrealty
June 7, 2012 at 5:22 pm
@DanTroup
Regarding HTTPs, Yes. I think the point is, it is funny when companies use “httpS” in part to seem more secure. But it isn’t so secure if you just let Google index it.
So you would rather AG hold onto the information for a few days, while more customers expose themselves, vs telling Docusign first to try and fix it? Fix it how? It isn’t like Docusign can immediately remove the information from Google and Google Cache.
Sure they didn’t leak the full contract. Well, as far as we know. Maybe they did. But leaking unpublished private email addresses and any details of a private contract is horrible. We have to trust these companies. I just found a colleague of mine. I bet she will NOT be happy that THREE of her transaction details (not the contract itself) are on Google. Three over 6 months.
Merge
June 7, 2012 at 6:01 pm
They should really be using a hash or id. It’s extra work to put the name in the url. I would be interested in hearing why they chose to do that.
I’m even MORE interested in why they allow indexing of those pages. It takes seconds to throw a robots.txt file up and keep search engines from seeing/indexing the pages.
joannasmitherton
June 7, 2012 at 7:01 pm
Hi folks:
AGBeat is trying to sell a story when there is no story. This is about people storing documents in public – OUTSIDE the DocuSign service. DON’T DO THAT. Many agents have been using public sharing folders to get documents back and forth to customers using tools that are not designed to protect them. THIS IS WHAT HAPPENS.
It has nothing to do with DocuSign security.
Biggest lesson – DON’T store documents outside DocuSign. If you do, make sure it is a secure location, or you will put your customer’s information at risk. (Not only the info about who signed, BUT THE DOCUMENTS ALSO)..
franklyrealty
June 7, 2012 at 7:08 pm
@joannasmitherton Are you referring to a document that one might download, save to their computer, and then upload to a shared location like Google Docs? That isn’t the case here.
These are on the Docusign servers!
So your lesson doesn’t make sense.
It was on their URL. I spoke to one agent that was very pissed that her email address was listed three times with three transactions over 6 months. And she claims she didn’t share anything. (maybe the other agent did, but that is a) stupid and b) shouldn’t be possible).
And if they did nothing wrong… why did they change it?
joannasmitherton
June 7, 2012 at 8:57 pm
@franklyrealty No, these documents are stored out in the open. That is the only way you could get to them. Since I don’t store documents outside DocuSign none of mine show up anywhere, I looked – used a whole bunch of names and emails we’ve done, and none show up. This is agents just not knowing that putting things on public shares makes them, well, public.
The information about who signed is NOTHING compared to the source data in the documents they stored outside in the open!! I’d be really pissed if my agent stored my documents in a public store also!
franklyrealty
June 7, 2012 at 9:06 pm
@joannasmitherton You still don’t get it.
Here was one example URL
https://www.docusign.net/Member/DocuSignTrust.aspx?veid=1dvf8mfgMUPc9PjJUdoAjP%2BdU3N30atFKhCztCBt1JccB6GHUUrg88%2FhfdvWLu6J&vdid=u8QahZ45NZs1DkME9UBVdOpQoz43cUjKNmVJr84OvdZZanq5k1smynT3oRju%2FHvF&vinit=joxDdQhwkrbMkc5UnLVckSdmfZ9yn9k4Lwhng5ULRX6fkVabgMlhona%2BsBW%2Fzhr1
Note that it starts with Docusign.net. It does NOT start with GoogleDocs.com etc
Of course now that Docusign has been alerted of the breach, they are trying to cover their tracks. Now that link has a firewall, but it didn’t before today. You can see the Cache version here. And explain to me what public place did these people put this private information?
Here is a similar link that breaks through the firewall (ie what it looked like yesterday)
https://webcache.googleusercontent.com/search?q=cache:Edw2hxa68NMJ:https://www.docusign.net/Member/DocuSignTrust.aspx%3Fveid%3DMr2QfVEWcKt%252FGbfkUYOr25rgolrnigh7dn1ecoR02ihpLW0NFvwmyD4%252BK%252F3%252Fh9yO%26vdid%3DXulfqqZ%252F4RAytumEOlDUYyKqx7Bz%252B8jNxnqmq2U1zdLo0H4seA7Cqzky%252BzWutxZy%26vsig%3DXCfdMXW3haMmhgS1Y00MzLCA1PwLAmxx2XuCEMETlprCbwYhHsUo89AYblYcPFDm+&cd=2&hl=en&ct=clnk&gl=us
BenspBenfb
August 30, 2012 at 6:42 pm
@franklyrealty @joannasmitherton Maybe they posted something like a signature receipt email that contained the link. So when google indexed that, they found the embedded link and followed it and then indexed that too. But you’d think we could find the original docs if they are all on public servers and were also indexed by google.
BenspBenfb
August 30, 2012 at 6:40 pm
@joannasmitherton What exactly did these DS customers put on their public web site that included such an odd unique link back to docusign’s system? Seems unlikely, but you never know…
franklyrealty
June 7, 2012 at 9:49 pm
I told my agents to stop using Docusign until the matter was resolved.
It appears that they found a solution to a problem they still deny existed. Now, moving forward, these private URLs will be blocked from Google via a firewall. That is great for the FUTURE, but still does not fix the approximately 10,000 users that were already indexed and still in Google’s Cache.
I demand that Docusign fess up (like Tylenol does when they mess up, albeit to a worse extent) and email ALL users about this glitch or at least email the 10,000 people that likely are NOT aware that their data was released to the public for Google.
How can we trust them if they just Deny Deny Deny. Remind me of a Chris Rock video: https://youtu.be/I28rarDdaCY?t=2m20s
One agent that was on there 3 times said she called Docusign and their response was “they have a team of people working on it and they know it’s a huge problem.” If it wasn’t a mistake, the answer should have been “yeah, you must have made it public, your fault not ours.”
It doesn’t matter how many ISO 9000s you have and 1, 2 3 parties that supposedly test your system, when you leave the front door open. I can have Brink’s Security on my house, but who cares if the door is left open.
Want to know if you are in there?
Here is how:
Google:
site:https://docusign.net “YOUREMAIL@YOURDomain.com” (with quotes)
or
site:https://docusign.net company name
and see what you find. And make sure you click on the CACHED version.
I just did a search and found a second friend of mine on there… they will not be happy. 2 so far.
I also found a few lawyers that have their info online. Asking them if they were stupid enough to have pressed some button to make it public. I really doubt it. And if they think it was stupid for Docusign to even allow that to happen (part of what they need to protect against is user error).
Frank
ArnCenedella
June 8, 2012 at 12:59 am
I like the docusign product and if there is a problem, I believe they will fix it.
Name and email address “breach” is a problem but it is not the end of the world. And I do believe it is possible, docusign users thru their own actions made the this data available.
It is also good reminder to us all that any data or info transferred over the Internet may not truly be safe.
I don’t think names and emails being “hacked” is a big deal.
I would think most folks who are on-line have emails addresses posted on the web already, right? Lots of folks are on line for either social or business reasons want their contact info posted and they want people to be able to contact them.
Property ow nerd hip records are public records and easily accessible.
franklyrealty
June 8, 2012 at 1:16 am
@ArnCenedella Correct. Not the end of the world.
You tell me. If you sent a Docusign to a client. To offer on a house. A bidding war lets say. And he comes to you and says “why is it that some/any details from our confidential contract ‘Offer on 555 Oak Street’ are posted on Google for all to see? Also it has my private email address and the GPS coordinates for my home where I signed, I am not happy.”
Are you going to tell them “Dear Sir, it is not the end of the world, get over it.”? I doubt that.
And no. Due to MASSIVE spam problems, I never post my email address ANYWHERE. So I would be very pissed if Docusign posted it online for spammers to have access to them. And yes there are web crawlers just out there looking to cultivate new email addresses to spam.
Yes they did change their system. They have yet to admit to fault or notify people that some/any of their data is online.
The worst part is this is just what was found. It begs one to ask what else is out there and Docusign hasn’t disclosed.
BenspBenfb
August 30, 2012 at 6:38 pm
@franklyrealty @ArnCenedella Yes, blaming their customers seems suspicious because there were so many. And then they managed to “fix” it and get Google to remove the links, something hard to do if the data being indexed wasn’t their own.
franklyrealty
June 8, 2012 at 1:22 am
Any Docusign competitors out there?
Anybody willing to chime in? Would your system EVERY allow your customer’s data (even if it is just an email, GPS location and contract name) to be accessible via Google, while still hosted on your URL?
If not, what steps do you do to prevent this?
franklyrealty
June 9, 2012 at 3:44 pm
Really disappointed that the Docusign competitors haven’t had the guts to come forward and state whether or not they had the same issue.
BenspBenfb
August 30, 2012 at 6:36 pm
@franklyrealty Well, it’s impossible to prevent your customers for disclosing their confidential information (purposely or accidentally). If they posted docs that contained the unique links (how did Google get those links anyway…there are so many instances it seems unlikely it was random users doing this). Of course, most sites would have a simple robots.txt that would keep Google (being honest right?) from indexing such a site. Otherwise, the link needs to be protected, but often the “protection” is just a unique link sent in an email that you expect only the owners to have and not have them submit it to Google for indexing. I wonder if that’s what really happened, Google indexing customer’s email? I’ve not heard of anybody else suffering this, though, so I still suspect it was DocuSign’s fault and not their customers who did something odd like post their unique links somewhere Google could index it.
AgentGenius
June 8, 2012 at 1:38 am
please see story updates, docusign explains how it’s not a security breach
DanTroup
June 8, 2012 at 7:42 am
@AGBeat, what made you think this was a security breach? You had evidence of someone breaking into DocuSign and stealing information? This is what a breach is. There is a huge difference between your story and other breaches in the news. Please don’t confuse the two. If someone wants to steal your car they have to break the window and hot wire the ignition. This is a great example of a breach. What you found, was data that was willing exposed. This is not a breach.
Anytime you find a security flaw your first step is to contact the company. Notifying the public first is just doing more damage. You draw attention to something where you don’t have control. For those that are thanking AGBeat, how are you fixing the issue? Are you calling all your clients letting them know? Are you removing their information from showing? You’re probably notifying them, but there is absolutely nothing you can do to resolve the issue. If there was something you could do to fix this issue then publishing the story would have been great. They could have included instructions for fixing the issue and you would have looked like a hero.
Merge
June 8, 2012 at 9:15 am
Dear Docusign & Docusign Developers,
Life might suck right now, but things will get better.
Hope this helps.
https://support.google.com/webmasters/bin/answer.py?hl=en&answer=1663660
I am a Sr. Developer, willing to chat/help just because I know what its like to be in a tough spot. No charge. If you ever need me just send a quick email to Joel (attt) MergeApp.com
nartech
June 13, 2012 at 4:39 pm
This is a good opportunity for me to make a pitch for the importance of privacy and data security in all contexts. (i.e. not just when using Docusign.) NAR has produced a data security and privacy toolkit to help you think about how you handle sensitive customer data. You can find it by following this link https://www.realtor.org/letterlw.nsf/pages/1010datasecurityprivacytoolkit?OpenDocument&Login
You must be a member of NAR and give your NRDS number to access the document.
unhacker
July 23, 2012 at 2:55 pm
Okay first off, yes as many have noted, this is not a “breach” as the term is generally used in Infosec. This is certainly a risk, but is probably best characterized as ‘disclosure’.
Most importantly, though, this information /was/ in fact retrieved from (or via) DocuSign’s own servers – if you doubt that, simply recognize that it was a change on DocuSign’s part that has closed this exposure. That’s because they (probably) have restricted Google from indexing that content. And that is what they should have done From Day One, Already.
This isn’t a breach: It’s evidence of a weak or lax back-end security posture, or procedures.
BenspBenfb
August 30, 2012 at 6:31 pm
@unhacker Technically this is correct, but allowing confidential pages to be accessible is bad form, and they did put a fix in to resolve it, showing that it was an error that could be fixed easily.
Ronie Walter @ IT Staffing Agencies
July 29, 2012 at 8:35 am
DocuSign moves the process of getting important documents signed completely online. Its tagging system shows the recipient what to do, and it offers a full court-accepted audit trail of the process. It’s a great choice for electronic signing of documents.
Pingback: Despite DocuSign promises, they couldn't avoid the inevitable - The American Genius