PwnedList database reveals your vulnerabilities
In recent years, hackers have made headlines for getting into major traditional news organizations, universities, government entities and the like, and even mainstream web users have learned that they are vulnerable to their email and Facebook accounts getting hacked. There is a universal understanding that everyone is vulnerable, but how can you actually know if your email has been hacked?
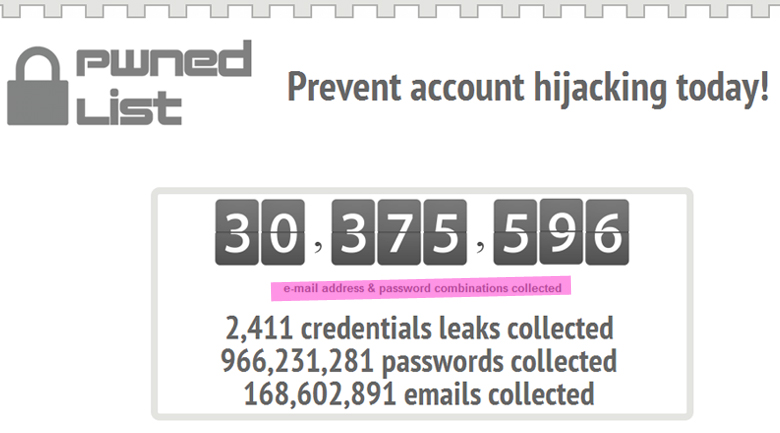
Just because your account isn’t sending out fake airline promotions or pharmaceutical ads to all of your contacts doesn’t mean you haven’t been hacked, so the simple way to know is to visit PwnedList which offers the largest database of stolen credentials as they grab data leaks when they happen – in other words, if you’ve been hacked, your email address is in their database.
Massive database and data transparency
Additionally, for the hacker types who are cynical about offering up their email address in search, PwnedList offers one-way SHA-512 hash which the company says is an anonymous way to check the database.
The company uses two sources of data for their massive database, which they are very transparent about. “One is the manual collection of data from account dumps made by various hacker groups. Every week we spend a fair amount of time researching possible new security breaches and trying to collect any resulting data dumps. The other source is our automated harvesting system that is able to spider certain places on the internet, identify potential account dumps and import them into our database, all without human intervention. In fact, almost 40% of our data comes from automated harvesting.”
Individual and end user protections
The company offers individual monitoring for free, and businesses are using the end user protection to secure their end user, already in use by one of the world’s largest social networks, banks, e-commerce, oil/gas/energy (to protect vital infrastructures), and security companies to enhance their own offering. In fact, it’s already being used by password management companies like LastPass and Dashlane which is a tremendous compliment to PwnedList’s reputation in the industry.
The first iteration of PwnedList began as a side project, and Co-Founders Steve Thomas and Alen Puzic worked with the hacker community to simply create a quick list of “am I included?” email addresses. From there it snowballed. In March 2012, the company launched their business service which focused on employees and beefed up their ability to collect leaks, adding sophisticated crawlers. Later in the year, the community pushed them to release monitoring for their end users since it’s their life blood, especially in light of fraud.
The Austin-based company operates on the lean startup method, is bootstrapped, and offers a simple, straight forward design wherein the focus is on the value, making it extremely easy for the average web user to understand it as well as a well educated hacker.
Showing a company’s true culture
When asked what readers’ key takeaway should be when reading about PwnedList, Co-Founder Steve Thomas didn’t focus on businesses signing up for their service or even searching for their email address, no, he said everyone should “use different passwords at different sites – hackers aren’t having to work that hard.”
Thomas urges people to help stop the domino effect, and essentially make their database empty. It’s a lofty dream, but the company’s true culture shone through in his answer, proving that their goal is to protect the people.
Lani is the COO and News Director at The American Genius, has co-authored a book, co-founded BASHH, Austin Digital Jobs, Remote Digital Jobs, and is a seasoned business writer and editorialist with a penchant for the irreverent.








































Pingback: A safe way to check if your email was compromised in a data breach - The American Genius Real Estate