Social media is filled with self indulgent people
Social media is a very prominent part of daily life and for the most part, it is a good thing. But, for some people, it becomes an outlet for vanity, overt self-endorsement, and an avenue for full disclosure.
Have you ever wondered if you are trying too hard to impress people when you navigate your social media channels? Are you obsessed with #selfies? Do you overuse emoticons? Now, there is a new way to tell if you are trying too hard.
![]()
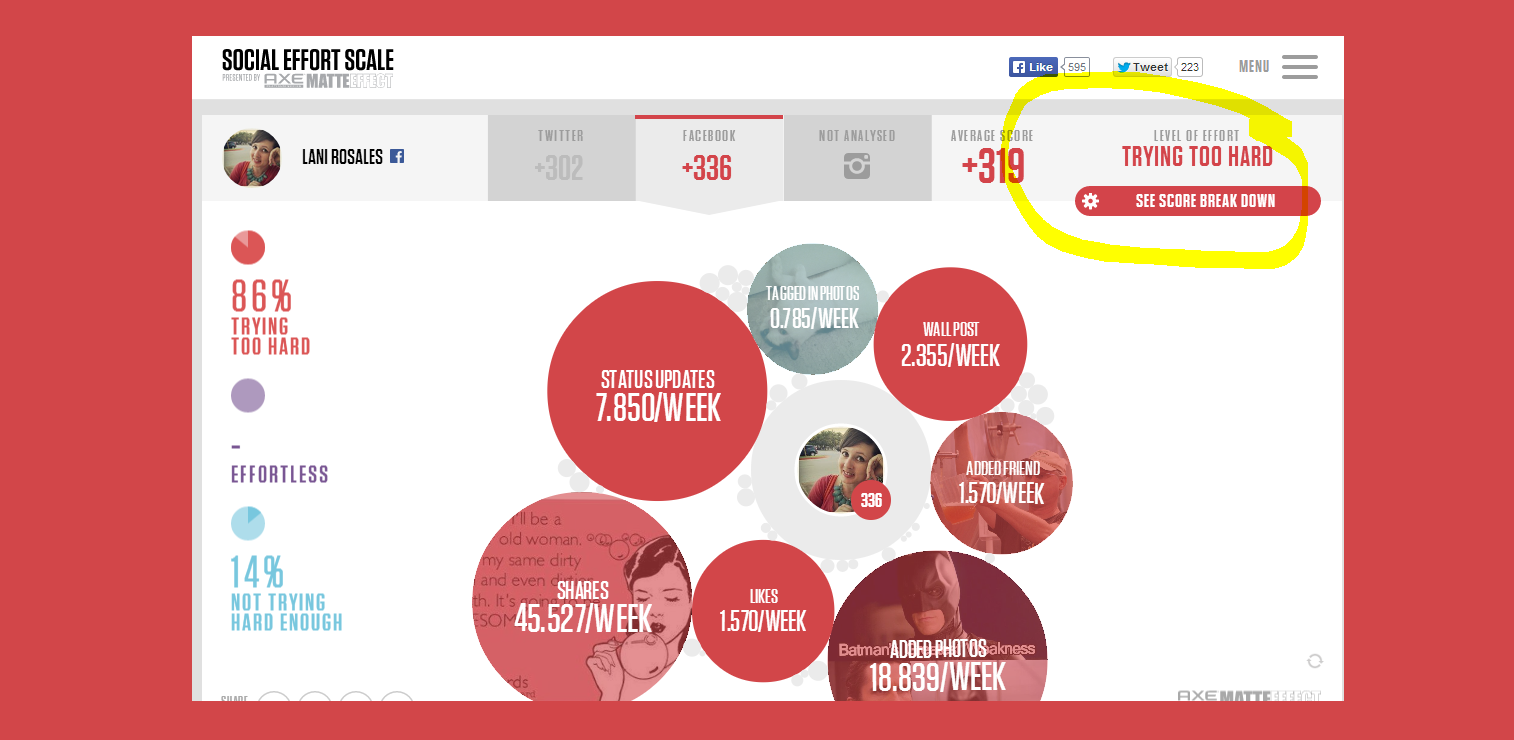
Axe, yes, the same Axe that makes deodorant and body spray, has created a new algorithm to measure your social efforts across your social media channels. Their new site, Social Effort Scale, analyzes your social media pages and gives you a score on whether or not you are trying too hard. They analyze how frequently you post, share, upload images, and add new friends. They also look at how often you use hashtags, emojis, and log in to your social media sites. You can analyze Facebook, Twitter, and Instagram. It will then analyze your last hundred Tweets, posts, or photo uploads.
So, it says I’m trying too hard…
I gave the algorithm a whirl and connected with my Facebook account. My score was 228: trying too hard. I blame my constant use of emoticons and sharing of movie trailers. When I connected my Twitter account, I received a score of 141: effortlessly cool. I find this a bit odd, because I have a tendency to overuse hashtags on Twitter, but I am sure there is more to this algorithm than meets the eye.
Once you have analyzed your profiles, you can connect with any of your friends to see what their scores are, as well as, the ability to view and compare your scores with other people worldwide; just click on the “see score breakdown” button at the bottom of your page.
While this is an interesting algorithm, I would not take it too seriously, especially considering they only analyze your last hundred posts. I do not feel like that is information to give them a full picture of what my social media use is really like, because some of us can post twenty times in a single day. Try it out for yourself though and see what score you receive.
Screenshot above of our COO’s score is used with her permission and good humor!
Jennifer Walpole is a Senior Staff Writer at The American Genius and holds a Master's degree in English from the University of Oklahoma. She is a science fiction fanatic and enjoys writing way more than she should. She dreams of being a screenwriter and seeing her work on the big screen in Hollywood one day.









































Scott Allen
June 17, 2014 at 3:31 pm
My Facebook was 312 and Twitter was 218…and I don’t even feel like I try hard at all.